 |
This is rather unpleasant. For one things, final fields aren't final. Even if a field is declared as a final, this loophole could allow another thread accessing the object might see the default value for the field. In all kinds of code, you would need to worry about whether the object a method is invoked on is properly initialized.
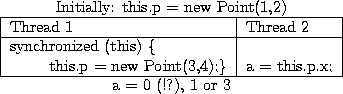
Note that synchronization isn't a magic fix to this problem. If we add synchronization to the update, but not to the read (as in Figure 10), we still have the exact same problem; both all writes need to be sent to main memory before the unlock action, but they can be sent in any order. You might think that putting a monitorexit between the creation of the Point and the storing of the Point into this.p might fix the problem; this is equivalent to making the constructor synchronized (see Figure 11). Unfortunately, this doesn't fix the problem either, because in the existing JMM, the write to this.p can be moved above the monitorexit instruction. The only way to fix this in the existing JMM is to require that the reader be synchronized.
Now of course, you can always say ``Don't write code with race conditions!'' But if you were writing a library that was sensitive from a security viewpoint, you would have to worry about other programmers using race conditions to attack your code. To fix this, we probably need to make all of the getFoo() methods synchronized (a getFoo() method is one that provides controlled access to a field/attribute Foo of an object). In the java.*, java.*.* and java.*.*.* packages of Sun's 1.2 distribution, there are a total of 829 getFoo() methods that return object references, of which only 26 are synchronized. Also, encouraging programmers to be very aggressive about using synchronization could also introduce more problems with deadlock.
I am convinced that we must fix this problem by making it possible to enforce an order on the writes. Trying to solve this problem solely by requiring synchronization whenever accessing shared data just isn't going to work.
I don't believe that there are any current Java implementations that could exhibit the behavior shown in Figures 9 - 11. As a result, few developers would bother avoiding idioms like that, feeling confident that they won't get bit. However, with advanced optimizing compilers and aggressive architectures, we might see this behavior down the road, at which point a huge codebase of unsafe code will exist.
Before trying to fix the problem, we should explore it in more detail. The basic problem in Figure 9 is that there are two writes to global memory that can be reordered, either by compiler optimizations or by the processor. There is no dependence forcing one write to come after the other, so the ordering is feasible and plausible unless we forbid it. If these writes are reordered, it could be detected by other threads, possibly with severe consequences. The reads might also be reordered, but this is more difficult because the memory location read by the second read is dependent on the value read by the first read.
In addition to arising in constructors, as shown in Figures 9 - 11, it also arises in the situations shown in Figures 13 - 15. If we are going to prohibit the anomalous behavior in Figures 9 - 11, we should also examine the behavior in Figures 13 - 15 and decide if they need to be prohibited.
I am not going to give a definitive answer. Instead, I will suggest several solutions, and discuss which behaviors they prohibit and their potential impact on compiler optimizations. My suggestions are roughly ordered from least protection/least cost to highest protection/highest cost, except making unlock a bidirectional write-barrier, which I consider a necessary prerequisite.
Once this change is made, Figure 11 can no longer exhibit anomalous behavior. You might try to fix the problems in Figures 9 - 10 by declaring the constructors as synchronized. Unfortunately, that isn't legal in Java. Without additional changes, the only solution would be to put synchronized blocks inside in each constructor. This would work, but it would be a substantial pain.
This will complete prohibit the behavior Figure 9. It won't completely prohibit seeing pre-initialized values for final fields. If a constructor passes this to another method before all of the final fields are initialized, the other method can see them (but this is an evil programming style). This doesn't prohibit any of the behavior in Figures 13 - 15.
The virtual machine could enforce a rule that the completion of a constructor acted as a write barrier, in the same way as a unlock action. This could apply to all constructors, or the spec might only require a write barrier at the completion of the outermost constructor (although putting one at the completion of every constructor would be allowed).
This is similar to allowing constructors to be synchronized. But since it doesn't actually lock the object, it couldn't possibly cause deadlock and would likely have minimal effects on performance. Thus, we don't have to worry about which constructors to synchronize; we just force a write barrier after every object is constructed. It also doesn't force a thread to empty the thread's working memory, so it may be less expensive than synchronization.
This approach is a little simpler to explain than rule a above, since it is simply explained in terms of actions. However, in code that created lots of light weight objects (particularly if the Java language is changed to provide better support for light weight objects than can be unboxed), the large number of memory barriers generated could significantly reduce the transformations that could be applied to the program.
We have a couple of options as to how strong we want this constraint to be. The basic, strong form of it is:
This would prohibit the anomalous behavior in Figures 9 - 14. We can relax this with any combination of the following two options:
One of the problems with enforcing this ordering is that we have to enforce it whenever a write might be to a field/element of an object being stored by the later write. Others I discussed this with expressed the opinion that this constraint should only be enforced if the writes involve the same variable, so that you know they reference the same object. In other words, if I write to p.x, then I write p into some variable, then I can't reorder the writes. However, if I write to p.x, and then I write q into some variable, than I can reorder them even though p and q might reference the same object. The problem with basing this constraint on variable names is that while variable names are fairly obvious in Java source code, they are not present in the Java virtual machine. When writing p, the value being stored comes off of the stack and might have gotten there through any number of stack manipulation instructions. Defining this constraint so that it only enforced the constraint when the same ``variable'' is involved would be very difficult to define and implement at the JVM level.
A decision to enforce one of these constraints should not be made without an understanding of the performance impact. Particularly due to the problem with aliases, the impact could be substantial (e.g., you would pretty much have to insert a write barrier before any store of an java.lang.Object, because it might reference any object that you have previously updated.
If we enforce this constraint only when the second write is to a volatile field, I suspect the performance impact will not be substantial. It makes a certain amount of sense, because if you are playing with data races, making your variables volatile is appropriate.